
A Guide to AWS Security Tools
By Dan Pfyl, Solutions Architect
Discover the different security tools and features offered by AWS and how they can help keep your organization safe.
With millions of customers in a wide range of sectors including government, healthcare, and financial services, AWS takes no chances when it comes to security. In the hyperscaler’s own words, it provides “security-specific tools and features across network security, configuration management, access control, and data security.”
Knowing what those tools are and how they work means you can safeguard your business with certainty. In this blog, we cover the different types of security tools and features offered by AWS, and how they can protect your organization’s infrastructure and data.
Connecting to AWS
There are essentially two parts to any cloud deployment: the compute, applications, and storage within AWS itself, and the way you connect to those resources within AWS.
There are two ways to connect to your AWS environment: a VPN over the internet, or via a private AWS Direct Connect using an AWS Direct Connect partner like Megaport.
Megaport is a NaaS provider allowing you to use our flexible network underlay to connect your private infrastructure to any service provider across our network, without the clutter. Integrate your entire architecture in just a few clicks to interconnect your private data center, branch offices, and remote users with a resilient, scalable, private connection to your AWS infrastructure.
Creating a secure connection to AWS
While each cloud provider offers a robust set of security features, there are other measures you should consider to secure your cloud environment first. Depending on the kind of business you’re operating, you may want to implement a combination of the below. Utilizing Megaport’s products and services will also ensure your security requirements are easy to meet.
Secure data center connectivity
Secure and private connectivity between your on-premises and cloud environments is a must. Using private interconnects to, from, and between data centers ensures that your data always stays on a reliable private protected path, minimizing exposure to attacks.
Virtual firewalls
Virtual firewalls act as gatekeepers between different segments of your network, allowing you to control traffic and protect your workloads from unauthorized access. With Firewall as a Service (FWaaS), you can easily deploy and manage these firewalls without the need for on-premises hardware.
For more information on how virtual firewalls can improve your security, check out our blog on Firewall as a Service.
Encryption in transit
Encrypting data while it’s in transit between your services or between your users and the cloud is essential. While cloud providers offer built-in encryption options, it’s crucial to ensure that data is encrypted not just at rest but also as it moves across the network. You can read more about different encryption options in our guide to encryption in transit.
APIs
APIs are the glue that holds together modern cloud applications, but they can also be a security risk if not properly managed. Securing your APIs with rate limiting, authentication, and encryption is key to ensuring that only authorized users and services can interact with your cloud environment.
Get our list of solutions to common API issues with Megaport.
Cloud Access Security Brokers (CASBs)
A Cloud Access Security Broker (CASB) is an on-premises or cloud-based security policy enforcement point, acting as an intermediary between your users and your cloud provider. This extra layer of security helps enforce your company’s security policies, monitor activity, and ensure compliance.
CASBs can also help you maintain visibility and control over your cloud services, even if your users are accessing them from outside your corporate network.
AI and automation
While using generative AI models and applications increase your organization’s attack surface, they can be used in your security strategy to provide a net positive.
According to IBM’s “Cost of a Data Breach Report 2024”, organizations that extensively use security AI and automation save an average of $2.22M USD in security-related losses.
Compare generative AI tools and platforms from the leading cloud providers.
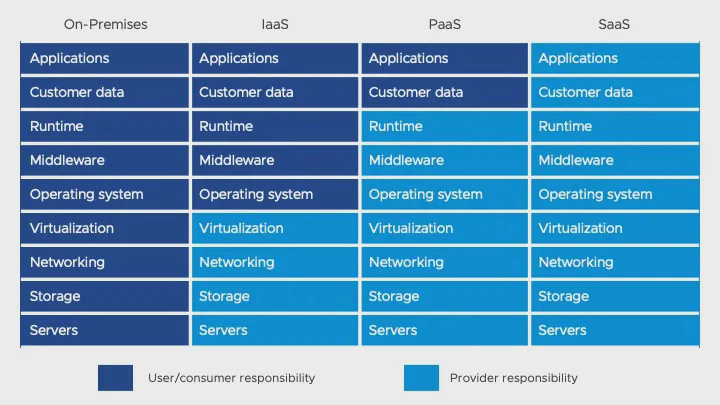
The shared responsibility model
Before reviewing the security features offered by AWS, it’s helpful to first understand the shared responsibility model of cloud security which delineates the security obligations expected of you versus your cloud provider.
Division of responsibility differs depending on whether you’re using Infrastructure as a Service (IaaS), Platform as a Service (PaaS), or Software as a Service (SaaS) security tools, but the core concept remains the same: Some aspects of security are up to you, and others are up to your provider.
Cloud providers are usually responsible for securing the infrastructure that runs their services; this includes the physical data centers, network hardware, and software they use to manage their cloud platforms. This is why cloud providers invest heavily in physical security, redundancy, and compliance certifications.
But while cloud providers will ensure their base infrastructure is safe from attacks, responsibly using that infrastructure falls on your shoulders. Part of this responsibility includes exploring the features and tools different cloud providers have to offer.
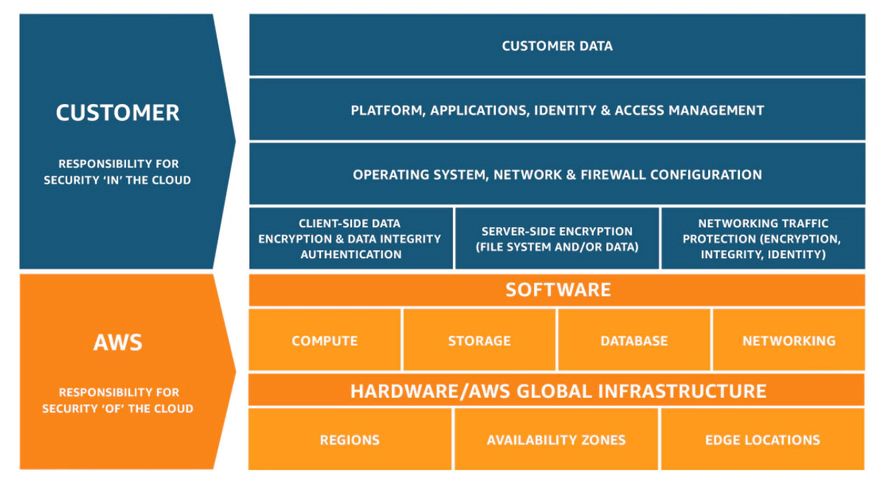
AWS’s approach to shared responsibility
According to its website, “AWS operates, manages, and controls the components from the host operating system and virtualization layer down to the physical security of the facilities in which the service operates. The customer assumes responsibility and management of the guest operating system (including updates and security patches) and other associated application software as well as the configuration of the AWS-provided security group firewall.”
About AWS security
With AWS, it’s important to know that there’s a difference between account security, and application and service security. Account security relates to protecting your workloads from unsecured identities – users, permissions, and general Identity and Access Management (more on that shortly). Application and service security, on the other hand, refers to the systems underlying your account, where cyberattacks take place.
You should deploy a combination of both security levels to safeguard your AWS workloads.
1. AWS Identity and Access Management
Purpose: Identity and access management
Security level: Account
Identity and Access Management (IAM) is a framework that governs which users can access which business resources, and how – it’s the foundation of solid account security.
AWS IAM provides granular access control by allowing you to create and manage permissions for users, services, and resources. It ensures that only authorized personnel have access to specific parts of your cloud environment.
More on AWS IAM2. AWS IAM Access Analyzer
Purpose: Identity and access management
Security level: Account
Additional to AWS IAM, IAM Access Analyzer moves you closer toward a “least privilege” setup—that is, where permissions are only granted where necessary for the completion of a task—by giving you the ability to set, verify, and refine your permissions.
More on AWS IAM Access Analyzer3. AWS Key Management Service
Purpose: Data protection
Security level: Application and service
AWS Key Management Service (KMS) allows you to create and control encryption keys used to encrypt your data both at rest and in transit, giving you full control over the encryption policies. By using KMS, you can achieve the highest level of encryption—up to the root key—in your data protection hierarchy, and every key will be safeguarded.
More on AWS Key Management Service4. AWS Config
Purpose: Detection and monitoring
Security level: Account
AWS Config helps you assess, audit, and evaluate your resource configurations and relationships. If you have multiple configurations to manage across your network, AWS Config makes it easy to troubleshoot and optimize them, as well as monitor and record changes for streamlined management.
More on AWS Config5. AWS Security Hub
Purpose: Detection and monitoring
Security level: Account
This cloud security posture management service automates and aggregates all of your security checks and alerts in a single platform. It can also monitor and identify potential holes in your network security to help you adhere to best practices, as well as give you a bird’s-eye visual of your security posture.
More on AWS Security Hub6. AWS IoT Device Defender
Purpose: Detection and monitoring
Security level: Application and service
Apply this security management tool across your IoT devices and fleets to quickly and easily find vulnerabilities. You can even set up alerts to notify you if unusual behavior is detected, and custom-define your traffic monitoring parameters.
More on AWS IoT Device Defender7. Amazon GuardDuty
Purpose: Detection and monitoring
Security level: Account
Amazon GuardDuty provides intelligent threat detection for your AWS accounts, workloads, and data, with continuous monitoring. With GuardDuty, you can respond to threats before they escalate and easily scale your threat detection across your AWS account suite.
More on Amazon GuardDuty8. Amazon Macie
Purpose: Data protection
Security level: Account
This data security service uses machine learning (ML) and pattern matching to discover and protect your sensitive data. Use it to strengthen your security posture, improve visibility, protect data during migration, and achieve compliance.
More on Amazon Macie9. AWS Secrets Manager
Purpose: Data protection
Security level: Application and service
AWS Secrets Manager helps you protect access to your applications and resources by easily rotating, managing, and retrieving database credentials, API keys, and other secrets. You can securely encrypt and centrally audit your secrets, rotate them automatically, or even replicate them for disaster recovery.
More on AWS Secrets Manager10. AWS Directory Service
Purpose: Identity and access management
Security level: Account
Designed for users of Microsoft Active Directory (AD), AWS Directory Service gives you access to your different AWS resources with seamless workload migration and integration. This advanced tool is perfect for customers looking to use Microsoft AD-aware or Lightweight Directory Access Protocol (LDAP)-aware applications in the cloud.
More on AWS Directory Service11. AWS Shield
Purpose: Infrastructure protection
Security level: Application and service
This managed DDoS protection service safeguards your applications running on AWS. With customizable protection, deep insights, and the ability to monitor up to 1,000 resource types, it’s designed to protect the availability and performance of your cloud workloads.
More on AWS Shield12. AWS CloudTrail
Purpose: Detection and monitoring
Security level: Account
Track user activity and API usage with AWS CloudTrail, an ideal tool for improving your hybrid cloud and multicloud security. CloudTrail helps you enable operational and risk auditing, governance, and compliance of your AWS account by aggregating and consolidating activity both within and outside your AWS environment, then providing detailed insights.
More on AWS CloudTrail13. AWS Health
Purpose: Detection and monitoring
Security level: Account
When events and changes impact your cloud resources, AWS Health will be your authoritative data source. This tool integrates with over 200 other AWS services to quickly notify you of operational issues or cloud changes, then provides you with actionable guidance you can take to remediate or prepare.
More on AWS Health14. AWS Web Application Firewall (WAF)
Purpose: Infrastructure protection
Security level: Application and service security
This web application protection tool safeguards against cyberattacks by enabling you to configure traffic rules based on custom-defined conditions. You can even create security rules that protect against bot traffic, SQL injection, or cross-site scripting.
More on AWS WAF15. AWS Certificate Manager
Purpose: Data protection
Security level: Application and service
If you use SSL/TLS certificates to encrypt network connections, AWS Certificate Manager (ACM) is an ideal management tool. You can more easily protect and obtain certificates, manage renewals, and get no-cost certificates for services integrated with ACM.
More on AWS Certificate Manager16. Amazon Inspector
Purpose: Detection and monitoring
Security level: Application and service
This automated security assessment service helps improve the security and compliance of applications deployed on AWS by scanning for vulnerabilities and recommending fixes. Amazon Inspector automatically discovers workloads including Amazon EC2 instances, containers, and Lambda functions, reducing unintended network exposure across your AWS environment.
More on Amazon Inspector17. AWS CloudWatch
Purpose: Detection and monitoring
Security level: Application and service
By collecting extensive data across your AWS resources and applications, AWS CloudWatch allows you to observe and monitor them in detail, respond to performance changes, optimize resource use, and give you insights into the operational health of your AWS network.
More on AWS CloudWatch18. Amazon Cognito
Purpose: Identity and Access Management
Security level: Account
Amazon Cognito is a scalable customer IAM tool that makes it easy for your organization to implement customer IAM into your web and mobile applications. Add user authentication and access control to your applications in minutes, with the option to add several more advanced security features to support compliance.
More on Amazon Cognito19. AWS Artifact
Purpose: Compliance
Security level: Account
AWS Artifact is your central repository for accessing and managing your AWS and third-party compliance reports. Perfect for supporting your next IT audit, this comprehensive tool makes it easy for you to find compliance reports, manage agreements, and assess independent software vendors (ISVs) on AWS Marketplace.
More on Amazon ArtifactGet more secure cloud networking with Megaport
As a trusted AWS Technology partner, Megaport’s private, elastic, and global network fabric is the perfect secure underlay for your AWS connectivity.
With Megaport, you can level up your network functionality and security in less than 60 seconds with solutions like:
- Hybrid cloud: Take your on-premises infrastructure direct to AWS in just a few clicks.
- Cloud-to-cloud: Spin up virtual routers to handle traffic between AWS and other cloud service providers.
- Edge networking: Deploy virtual PoP solutions including SD-WAN gateways, virtual routers, and virtual firewalls, anywhere in the world.
- Data Center Interconnect: Our secure point-to-point service creates a Layer 2 connection between any two data centers in our expansive global ecosystem.
- Megaport Internet: Get a dedicated internet solution with all the benefits of Megaport’s scalable network fabric in just 60 seconds.
- Megaport AI Exchange (AIx): Interconnect all of your AI infrastructure, workloads, and providers including GPUaaS providers, third-party models, and storage and compute.
Whether it’s virtual firewalls, encryption in transit, or secure cloud interconnections, Megaport helps you achieve a more secure cloud environment.


